CBS News Live
CBS News Texas: Local News, Weather & More
Watch CBS News





They found him guilty – now four jurors are explaining how they were convinced to convict Dr. Raynaldo Ortiz.

Civil rights icon Opal Lee will receive an honorary Doctor of Humane Letters degree from Southern Methodist University.

"If we were to lose control of the Corporation and its assets it would allow the Defendants to remove us from our home, as they have already threatened to do," the Rev. Mother wrote. "I pray they be stopped."

Daniel Olalde Moreno's family was heartbroken about his death in connection to a prom afterparty in Fort Worth. Meantime, police are trying to find his killer.

"My hope is that this war ends soon, that we can come to a peaceful resolution that is equitable for all, and that we all recognize each other's similarities so that we cannot just see the differences."

One person is seriously hurt after crashing into a DART train Monday night near the MLK Station.

Harris says his female neighbor was walking up to his yard when he says a group of 8 pit bull mixes ran off his property and violently started attacking her.

More heavy spring rain is in the forecast and is expected to arrive between Friday and Saturday.
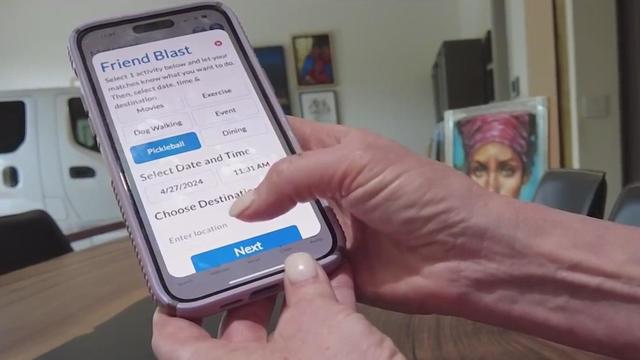
Feeling lonely can be a bummer, but according to the Surgeon General, it can also kill you.

CBS News Texas watched surveillance video from a triple shooting connected to a prom night after party in Fort Worth. There are at least 12 seconds of gunfire as people scatter to safety.

"We are not things to be traded or given away in backroom deals," the nuns wrote in a four-page response to the decree posted to their website Saturday afternoon.

Bois D'Arc Lake is now open to families, boaters and fishers just an hour northeast of DFW in Fannin County.

More heavy spring rain is in the forecast after the record rain at DFW and Love Field on Saturday (2.34" and 4.22"). It looks to arrive sometime between Friday and Saturday.

Civil rights icon Opal Lee will receive an honorary Doctor of Humane Letters degree from Southern Methodist University, the university announced.
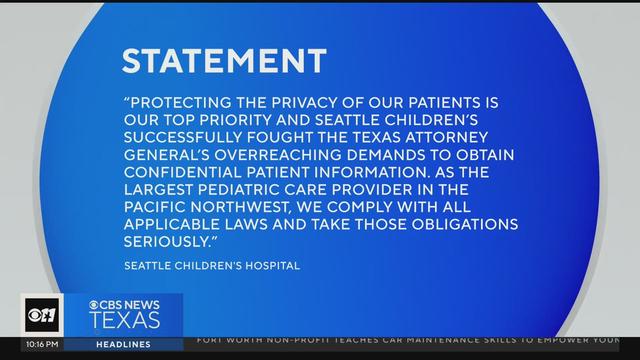
In November 2023, Paxton opened an investigation into Seattle Children's Hospital. The Attorney General says the hospital did not comply with requests for documents and the institution sued Texas.

Authorities say a second person has died after a man plowed a stolen 18-wheeler into a driver's license office nearly two weeks ago in Brenham. The Washington County District Attorney's office and the Department of Public Safety confirmed a 63-year-old woman died from injuries stemming from the crash. Authorities say the driver, Clenard Parker, intentionally rammed the truck into the DPS office. They say Parker was upset about not getting his CDL renewed the day prior.

Anthony Johnson's family wants to know why the media knew more about his death than they did.

More heavy spring rain is in the forecast after the record rain at DFW and Love Field on Saturday (2.34" and 4.22"). It looks to arrive sometime between Friday and Saturday.
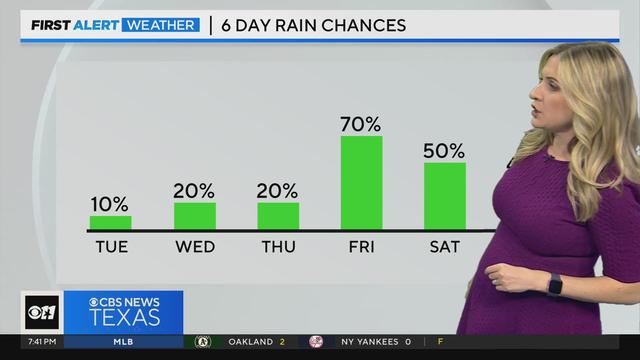
Over the next three days, brisk south winds are expected to bring the humidity back up. There are slight rain/storm chances for Tuesday and Wednesday. These chances start increasing on Thursday night.

More heavy spring rain is in the forecast and is expected to arrive between Friday and Saturday.

Texas police departments have the discretion to determine the frequency and extent of additional driving training for their officers. While some require driving training yearly or every other year, others do not.

Some departments opt to melt the firearms down, while others choose to crush them. However, there are instances where firearms, or at least parts of them, escape destruction altogether.

Several police departments told the CBS News Texas I-Team they were unaware of this practice, even though it was stated in the contracts they signed with the company, Gulf Coast GunBusters.

It's a complicated process that not everyone qualifies for.

Tuesday, federal prosecutors called their first witnesses against Dr. Raynaldo Ortiz.

The teams were meeting in the playoffs for the third time in five years, with the Clippers having won both previous series.

The Dallas Cowboys have signed free agent running back Royce Freeman.

An attorney for the accuser says they plan to refile the lawsuit in Collin County.

Michael Lorenzen pitched five spotless innings in his Texas debut and three relievers completed a five-hit shutout as the Rangers topped the Detroit Tigers 1-0.

Caitlin Clark has been selected with the No. 1 pick in the WNBA draft by the Indiana Fever.

They found him guilty – now four jurors are explaining how they were convinced to convict Dr. Raynaldo Ortiz.

Civil rights icon Opal Lee will receive an honorary Doctor of Humane Letters degree from Southern Methodist University.

"If we were to lose control of the Corporation and its assets it would allow the Defendants to remove us from our home, as they have already threatened to do," the Rev. Mother wrote. "I pray they be stopped."

Daniel Olalde Moreno's family was heartbroken about his death in connection to a prom afterparty in Fort Worth. Meantime, police are trying to find his killer.

"My hope is that this war ends soon, that we can come to a peaceful resolution that is equitable for all, and that we all recognize each other's similarities so that we cannot just see the differences."

They found him guilty – now four jurors are explaining how they were convinced to convict Dr. Raynaldo Ortiz.

Texas police departments have the discretion to determine the frequency and extent of additional driving training for their officers. While some require driving training yearly or every other year, others do not.

Some departments opt to melt the firearms down, while others choose to crush them. However, there are instances where firearms, or at least parts of them, escape destruction altogether.

Several police departments told the CBS News Texas I-Team they were unaware of this practice, even though it was stated in the contracts they signed with the company, Gulf Coast GunBusters.

It's a complicated process that not everyone qualifies for.

Starting in September of 2024, the year-long residency will allow new teachers to work with veteran teachers before taking on their own classroom.

A bill that could ultimately ban TikTok in the U.S. will soon head for a vote in the Senate. Here's what experts say to expect next.

The bond includes upgrades to city streets, parks and public safety facilities. The largest single ticket item in this year's bond includes $50 million for the newly proposed Dallas Police Department's new training facility.

People who have experienced extreme weather are especially likely to say climate change needs to be addressed right away.

Every week, Eye on Politics breaks down some of the biggest political stories grabbing headlines in North Texas and beyond.

Self-driving 18-wheelers have longtime truckers worried about their livelihood and others concerned that the technology needs more testing to make sure the public is safe.

McDonald's concept restaurant CosMc's has taken its drink-focused menu to Dallas for its second-ever location.

With the country on the cusp of greeting the return of spring, a warm-weather treat is once again available for free for a limited time only.

Kelli and Michael Regan were looking for a new dog. The breeder they found online asked them to pay with gift cards.

Target, looking for ways to add sales, is relaunching its Target Circle loyalty program including a new paid membership with unlimited free same-day delivery in as little as an hour for orders over $35.

The CDC estimates the U.S. could reach 300 measles cases in 2024 — more than the recent peak two years ago.

Organic option is best when buying certain produce, especially blueberries, nonprofit group says in analysis of chemical residues.

The $872 million most likely excludes any amount UnitedHealth may have paid to hackers in ransom.

George Schappell and sister Lori, of Reading, Pa., were the world's oldest conjoined twins, according to the Guinness Book of World Records.

Most worrisome gaps involve cancer chemotherapy drugs, ER medications and and therapies for ADHD.

The projects are expected to create at least 17,000 construction jobs and 4,500 manufacturing jobs.

After more than 40 years in business, 99 Cents Only Stores, a discount chain, announced on Thursday that it will close all 371 of its locations and cease operations.

"This is huge, HUGE! If we don't plan appropriately, A, we won't have workers. Or B, we'll have so many people on the streets that nobody can get to the events."

"This is going to be an event all the way through the weekend, even starting as early as Friday."

Federal officials say milk from dairy cows in Texas and Kansas has tested positive for bird flu.

The teams were meeting in the playoffs for the third time in five years, with the Clippers having won both previous series.

The Dallas Cowboys have signed free agent running back Royce Freeman.

An attorney for the accuser says they plan to refile the lawsuit in Collin County.

Michael Lorenzen pitched five spotless innings in his Texas debut and three relievers completed a five-hit shutout as the Rangers topped the Detroit Tigers 1-0.

Caitlin Clark has been selected with the No. 1 pick in the WNBA draft by the Indiana Fever.

Mary J. Blige, Cher, Foreigner, A Tribe Called Quest, Kool & The Gang, Ozzy Osbourne, Dave Matthews Band and Peter Frampton have been named to the Rock & Roll Hall of Fame.

Taylor Swift broke her own records, Spotify said, and now owns the record for the top three most-streamed albums in a single day.

The singer was found deceased at her home, a representative said.

Anticipation was growing at a fever pitch before Taylor Swift's latest album, "The Tortured Poets Department," dropped at midnight EDT. But it turned out it's actually a double album.

The singers first dated in 2003 and delighted fans when they rekindled their relationship in 2023.

More heavy spring rain is in the forecast after the record rain at DFW and Love Field on Saturday (2.34" and 4.22"). It looks to arrive sometime between Friday and Saturday.

Civil rights icon Opal Lee will receive an honorary Doctor of Humane Letters degree from Southern Methodist University, the university announced.

In November 2023, Paxton opened an investigation into Seattle Children's Hospital. The Attorney General says the hospital did not comply with requests for documents and the institution sued Texas.

Authorities say a second person has died after a man plowed a stolen 18-wheeler into a driver's license office nearly two weeks ago in Brenham. The Washington County District Attorney's office and the Department of Public Safety confirmed a 63-year-old woman died from injuries stemming from the crash. Authorities say the driver, Clenard Parker, intentionally rammed the truck into the DPS office. They say Parker was upset about not getting his CDL renewed the day prior.

Anthony Johnson's family wants to know why the media knew more about his death than they did.

Dallas artist Roberto Marquez traveled to the Rafah Crossing in Egypt, the U.S. capital and will attend this weekend's statewide protest in Austin.

On Friday, hundreds of thousands of fans gathered outside and all around Globe Life Field in Arlington to celebrate the Texas Rangers historical World Series win!

Babies in the neonatal intensive care unit at several Texas Health hospitals were dressed in creative costumes for Halloween.

Is that the smell of cotton candy, beignets and brisket wafting over Fair Park? It sure is, and we are here for it!

No one puts these dolls back in their boxes. Babies in the neonatal intensive care unit at Texas Health Harris Methodist Hospital Southwest Fort Worth are pretty in pink!